Verifiable Credentials: A Glossary (For Everyone)
As you learn more about identity management and the wallet ecosystem, you’ll come across concepts related to verifiable credentials. This terminology is sometimes hard to understand, especially if you're not well-versed in technical jargon and just starting to familiarize yourself with the topic.
Fear not!
In this article, we’ll explain the most common terms in a way everyone can understand.
Credential
In the physical world, credentials are already a part of our daily lives in the form of passports, driver's licenses, health insurance cards, university degrees, and so on.
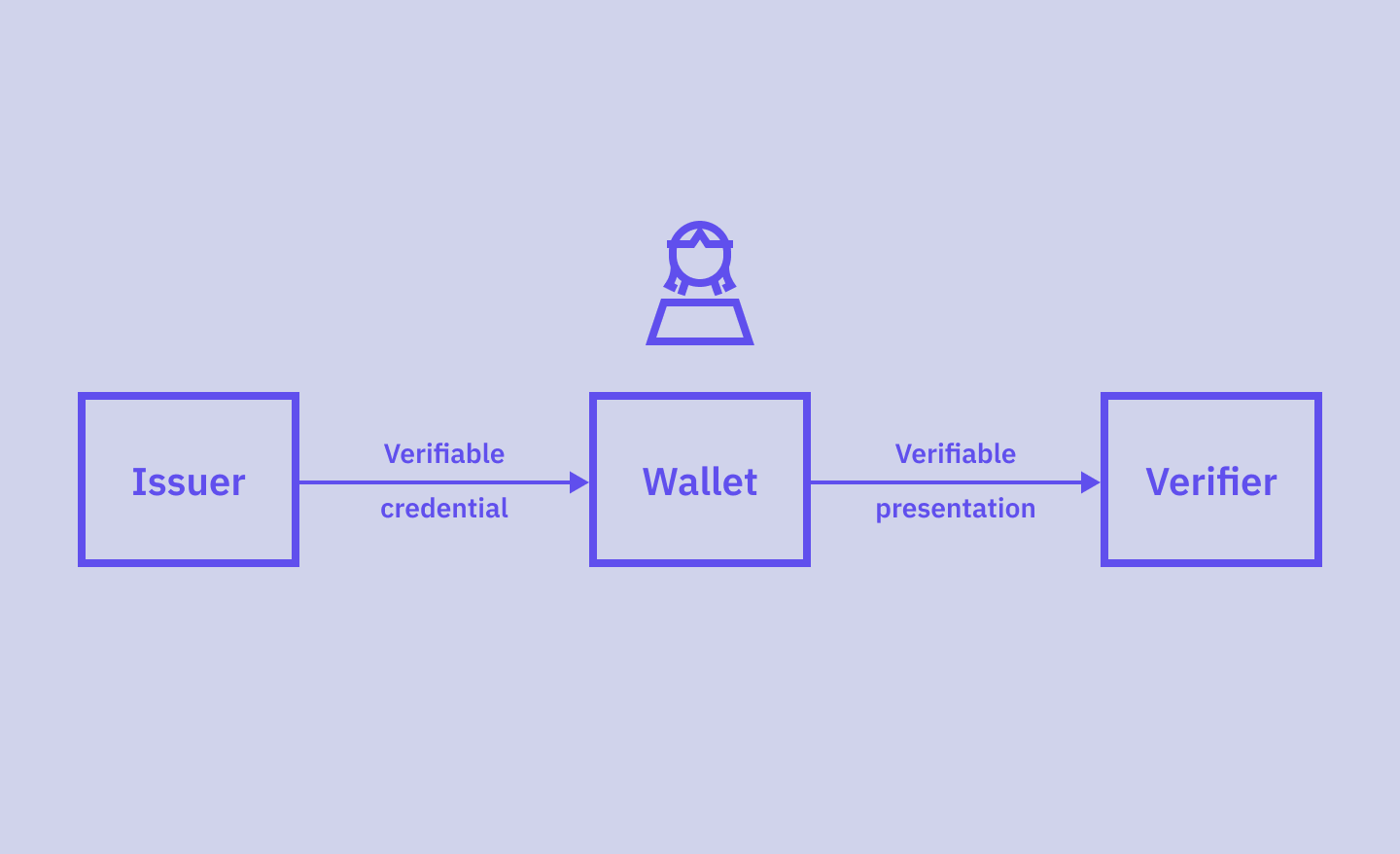
Verifiable Credential (VC)
A credential becomes a verifiable credential once it's in a standardized digital format and can be verified cryptographically.
Definition: Verifiable credentials follow the W3C Verifiable Credentials Data Model. A verifiable credential can hold much the same data as a physical one, yet it's protected by cryptography to ensure integrity and prevent tampering.
The three basic components of a verifiable credential are:
- Metadata: This contains background and details about the credential to help understand where the credential comes from and what it is for.
- Claims: Statements made by the issuer (the entity giving the credential) about the person it's issued to. It could be things like name, age, or qualifications.
- Proofs: Cryptographic evidence to confirm that the credential is real and hasn't been changed. The math behind the proofs guarantees the credential is genuine and comes from a trusted source.
In simple terms: Just as physical credentials, verifiable credentials are issued to individuals (holders) by trusted entities (issuers). The holders can use these credentials in the future to prove their identity.
Because of the cryptographic proofs contained in the credentials, the party that receives them (the verifier) can immediately check three critical aspects:
- The integrity of the credential
- That it was issued by a trusted issuer
- That it was presented by the rightful holder
That’s where the "verifiable" part of the name comes from.
Imagine your driver's license in digital form. Just as your physical license comes from a trusted authority, a verifiable credential is issued by a trusted organization and digitally signed for authenticity. You can then present it to any verifier that requires it: a government authority, a local business, or your bank—just as you would in the physical world.
University degrees, boarding cards, electronic identities issued by banks/governments (like eIDs used today) can all be verifiable credentials, as long as they adhere to the W3C standard.
Presentation (or Verifiable Presentation)
Definition: Data from one or more verifiable credentials that is presented to a specific verifier. The presentation may use selective disclosure so that the holder only shares a subset of the credential information. A presentation is verifiable when it provides Cryptographic Holder Binding.
In simple terms: Imagine you have a digital wallet with various credentials inside. When you need to prove, say, your educational qualification, you can choose to only show the relevant degree information from your academic transcript instead of revealing every other detail.
Issuer
Definition: An entity that creates and issues verifiable credentials.
In simple terms: An organization, authority, or business responsible for issuing your digital credentials, like your university, a government agency, or a bank.
Holder
Definition: The individual or entity to whom the verifiable credential belongs.
In simple terms: That's you! The person holding or using the digital credential.
Verifier
Definition: An entity that receives and verifies the verifiable credential.
In simple terms: Any party requiring proof of your credentials, such as a potential employer or a service provider. Interestingly, one entity can act as both an issuer and a verifier. Picture, for instance, your go-to e-commerce platform: it can first issue you a digital credential for online login and later verify this credential when you log in to your account. Rather than storing your private information in their own database, they request it from your wallet when necessary. This approach greatly enhances user privacy and ensures compliance with GDPR regulations.
Claims
Definition: Claims in a verifiable credential are pieces of information about the holder, such as their name, age, or qualifications (a lot like JWT claims).
In simple terms: Claims are similar to the details found on a physical ID card. They provide information about the person the credential belongs to, like their name, citizenship, or title.
Proofs
Definition: Cryptographic evidence that demonstrates the authenticity and integrity of a verifiable credential. Various forms of digital signatures are commonly used as proofs.
In simple terms: When issuing a verifiable credential, the issuer signs it with a digital signature, adding a unique cryptographic stamp to verify its authenticity. An analogy in the physical world is the original stamp of your university attached to your diploma. The math behind the cryptographic proof ensures that the credential is genuine and has not been tampered with.
Revocation
Definition: The process of invalidating a previously issued verifiable credential.
In simple terms: If your digital credential gets stolen or you lose access to it, revocation ensures it can't be misused by someone else.
Zero-Knowledge Proofs
Definition: A cryptographic method where one party can prove to another party that a statement is true without revealing any information beyond the validity of the statement. This involves complex mathematical algorithms that ensure the integrity of the proof while keeping the original statement secret.
In simple terms: Picture this: you want to prove you're old enough for something without giving away your exact age. Zero-knowledge proofs let you do just that. You can confirm you meet the requirement without disclosing any unnecessary details, like your date of birth. When a verifier asks if you are above, say, 21, they will only receive a Yes/No response.
Selective Disclosure
Definition: The ability for holders to only share part of the information in a credential issued to them.
In simple terms: Selective disclosure means you can choose which details you share from your digital credentials. For example, if you're applying for a job online, you might only share your full name and professional qualifications from your digital resume, keeping your contact information and personal address confidential until later stages of the application process.
Selective disclosure will not be available for all verifiable credentials: This depends on the specific implementation details.
SD-JWT-based Verifiable Credentials (SD-JWT VC)
Definition: SD-JWT VC is a verifiable credential based on the SD-JWT format, which enables selective disclosure. SD-JWT is a fundamental component in the latest EUDI Wallet Architecture and Reference Framework and has experienced a significant rise in adoption across Europe.
In simple terms: Verifiable credentials can be expressed in various formats, and SD-JWT VC is one such format. Its main characteristic is that it enables selective disclosure, although it can also be used when there are no claims requiring selective disclosure.
Cryptographic Holder Binding
Definition: Cryptographic holder binding is the process of confirming that a credential was issued to a particular holder through cryptographic assurance. It guarantees that only the rightful owner can present and utilize the credential.
In simple terms: It enables verifiers to trust that the individual presenting a credential is the same individual to whom the credential was originally issued. So when you’re presenting a credential, the verifier can trust it belongs to you and hasn’t been copied or cloned from another holder’s wallet.
Digital Wallet
Definition: A digital application or service that lets you securely store and manage verifiable credentials, making it easy for individuals to access and present their credentials when necessary. "Repository" (or “credential repository”) is another term for a digital wallet.
In simple terms: Digital wallets are necessary to store verifiable credentials. Think of a digital wallet as a secure place for keeping and managing your digital IDs and certificates. It provides a safe environment where you can easily access and share these credentials whenever required. Similar to how you keep your driver's license and other important cards in a physical wallet, a digital wallet serves as a repository for your digital identity assets.
Federated Identity Model
Definition: The federated identity model allows users to access multiple applications using a single set of login credentials. It relies on trust between an Identity Provider (IdP) and a Service Provider (SP). The IdP creates and manages user credentials, and the SP and IdP agree on the authentication process. As a result, with federated identity, users can access various online platforms without having to log in separately each time. Signing in this way is also known as “single sign-on”.
In simple terms: In this model, there is an identity provider (IdP) that maintains user data and provides proof of identity, and a service provider that consumes the data. A classic example is Google's system. If you have a Google account, you can use it to log in to different services like YouTube and Gmail, as well as other websites. The same applies to using Facebook or Apple credentials to sign in to other apps. However, this ease of use comes at a cost: these companies track your login activity and use this data for targeted advertising and building a comprehensive online profile. Moreover, should your password be compromised, all the other platforms linked to your single sign-on account might become vulnerable.
Decentralized Identity Model
Definition: With the introduction of verifiable credentials, the federated identity model is giving way to decentralized identity. In this new model, issuing organizations create and issue credentials, and verifying organizations can instantly check their authenticity. Individuals are in control of their identities, managing and using their credentials autonomously.
In simple terms: In decentralized identity, there's a credential issuer, a verifier, and a wallet acting on behalf of the user. In practice, it means your identity data is stored securely in your own wallet, not on some distant corporate server replicated across various platforms. Unlike the federated model where data flows directly from issuer (identity provider) to verifier (service provider), here, you receive and store credentials in your wallet, deciding when and how to present them. This setup enhances user privacy, as issuers are unaware of where the credentials are being used.
OpenID (or OpenID Connect)
Definition: OpenID is an open standard and authentication protocol designed to verify user identity and retrieve user profile information in an interoperable manner. It enables users to access various web applications using a single set of credentials. Historically used for federated authentication, OpenID is renowned for its simplicity, security, and widespread adoption. As decentralized identity takes over, OpenID will continue to play a significant role in this new ecosystem.
In simple terms: For instance, when you log in to a website with your Google or Facebook account, you’re leveraging federated authentication, with OpenID as an underlying technology.
OpenID4VCI (or OpenID for Verifiable Credential Issuance)
An extension to the OpenID ecosystem, this specification defines a protocol for issuers to issue credentials directly to holders, or for holders to request a credential from an issuer.
OpenID4VP (or OpenID for Verifiable Presentations)
Another extension to the OpenID ecosystem, this specification defines a protocol that lets verifiers request presentations from holders.
Navigating the Identity Space with Criipto
Digital wallets will soon become widely available through businesses, our governments, and our employers, and veritable credentials are about to become mainstream.
Criipto is working on new offerings within the identity space.
We’re looking to rethink and adapt to changes in how users experience and perceive identity solutions.
And we’re hiring!



