Trusted Timestamping: Comprehensive Guide & Use Cases

The practice of timestamping information has a long history. Centuries ago, scientists and inventors like Galileo and Robert Hooke used anagrams and encoded messages to claim the authorship of their discoveries. Much later, in the days of the printing press, office workers timestamped documents using physical stamps with clocks attached to them.
In our digital age, timestamping has evolved into a well-established technology. This article explores the fundamentals of trusted timestamping, its technical aspects, and practical applications.
What is trusted timestamping?
Trusted (digital) timestamping is the process of assigning a unique identifier to a specific digital event or transaction. It provides a reliable, immutable record of the event’s date and time and includes the metadata necessary to verify the authenticity and integrity of the timestamped data.
Timestamps can be applied to messages, documents, transactions, software, and other types of data.
Trusted timestamping is needed because of the inherent vulnerabilities of the Internet and digital systems, where information is prone to tampering and manipulation.
For instance, say you receive an important electronic document from a colleague. You might want to know when this document was created or last modified, But you can't fully trust the time shown on the document, because the author's device clock might be incorrect or intentionally altered.
In such cases, trusted timestamping offers a solution by ensuring that the date and time associated with the document's creation or modification cannot be manipulated or forged. This is achieved by introducing an additional actor: a trusted third party.
According to the RFC 3161 standard, a trusted timestamp is one issued by a Trusted Third Party that acts as a Time Stamping Authority. Its primary role is to confirm that specific data existed at a particular moment in time while ensuring that no one – including the author – has the power to alter or backdate the timestamp.
What is a Time Stamping Authority (TSA)?
Think of a Time Stamping Authority as the digital equivalent of a notary for online documents.
A TSA is typically a server running timestamping software. Timestamping servers often employ a high-performance hardware security module (HSM) for enhanced performance, reliability, and tamper resistance.
TSAs undergo regular audits and adhere to regulatory standards, such as eIDAS in Europe, the Electronic Signatures in Global and National Commerce Act (ESIGN), and the Uniform Electronic Transactions Act (UETA) in the US.
You can find a list of free and publicly available TSAs that conform to RFC 3161 standards here.
RFC 3161 and its extension RFC 5816 are standards for secure cryptographic timestamping, defining what products and organizations must include in timestamps.
How does trusted timestamping work?
Trusted timestamping, as defined in RFC 3161, relies on public-key cryptography.
In a nutshell, to generate a timestamp, the TSA cryptographically binds the unique hash of the data with the current date and time, synchronized with a trusted time source. The result is then signed with the TSA’s private key.
Here's the process:
- To initiate the process, the data author (or requester) calculates a cryptographic hash of the data that requires timestamping. Only a hash of the data is sent to the TSA, so the data itself remains secret.
- The hash is sent to the TSA in a timestamp request. The timestamp request also includes the object identifier of the hash algorithm used, the version of the timestamp request, a nonce, and other metadata.
- TSA adds the current time to the data hash, which creates a new combined hash.
- The new hash is signed with the TSA's private key. The TSA’s digital signature concatenated with the new hash forms a timestamp token.
- The timestamp token is returned to the requester.
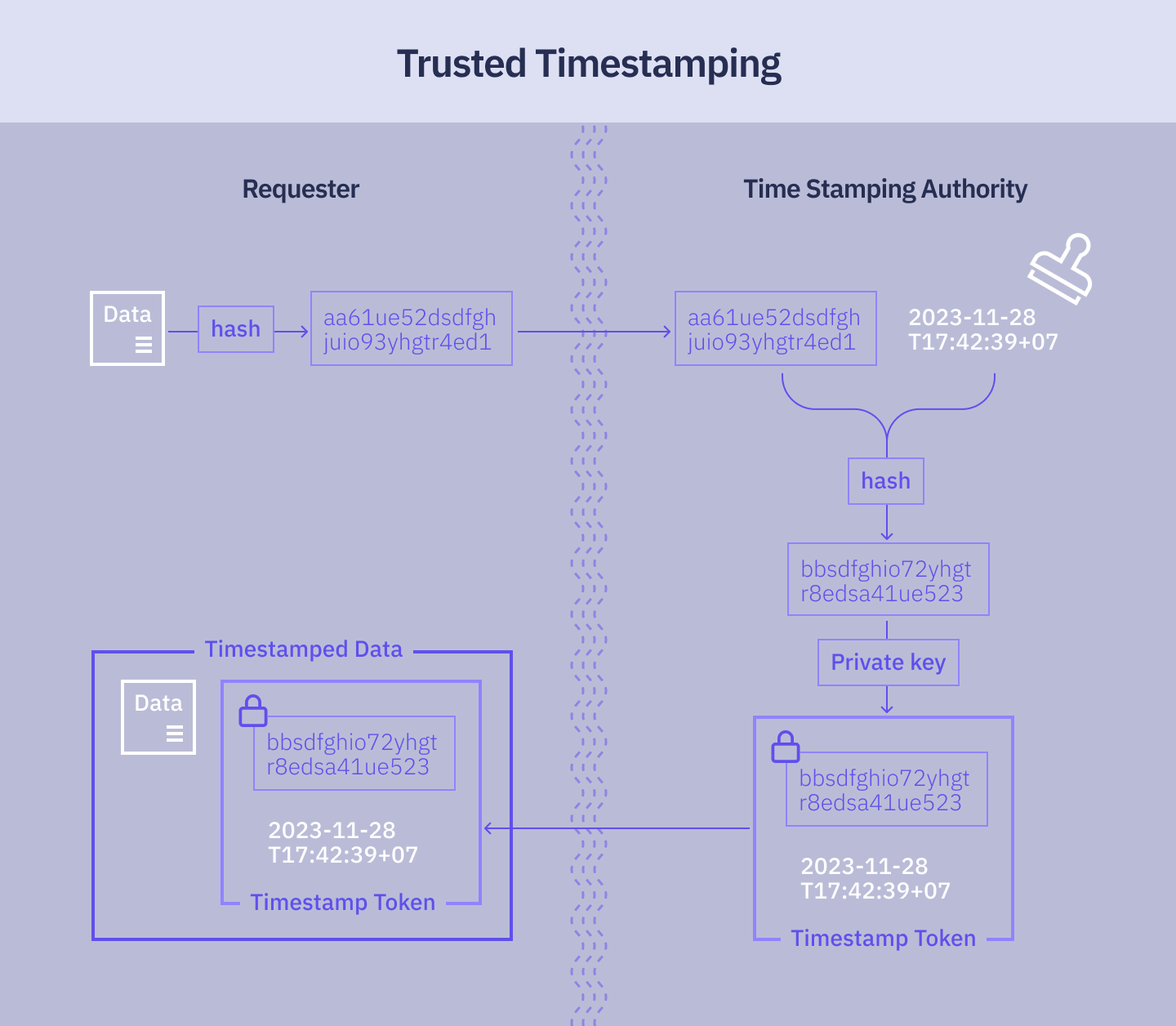
The requester then stores the original data and the timestamp token together.
When the data is accessed, the validity of the timestamp can be checked.
How to verify a trusted timestamp
To verify a trusted timestamp, a verifier needs three elements: the hash of the original data, the timestamp token, and the TSA's certificate.
1. First, the hash of the original data is calculated and compared with the hash in the messageImprint field of the timestamp token. If the hashes match, this confirms that the data remained unchanged since the time of timestamping.
2. Next, the TSA’s signature is validated against the TSA’s certificate to confirm that the timestamp was indeed issued by the TSA.
3. The final step involves confirming that the certificate chain can be traced back to a trusted root and that the TSA’s certificate hasn’t been revoked. The TSA’s certificate has to be valid during the verification process to maintain the trustworthiness of the timestamp.
If all checks pass, this confirms that the timestamp was issued by the TSA and that the data hasn’t been altered since the time of timestamping.
How to perform RFC 3161 timestamping
One advantage of RFC 3161 timestamping is that it adheres to the Internet X.509 Public Key Infrastructure Time-Stamp Protocol. This is a widely supported standard, which means RFC 3161 timestamps can be obtained and verified using numerous tools. Below are three options, ranging from advanced to user-friendly in technical complexity.
- OpenSSL: one of the most versatile options is to leverage OpenSSL – a widely-used open-source toolkit that specializes in cryptographic operations. This article provides a helpful step-by-step example.
- Timestamping library: you can choose one of many libraries that adhere to the RFC 3161 protocol to perform timestamping programmatically, such as the rfc3161ng library. Timestamping for git repositories can be implemented with GitTrustedTimestamps.
- Timestamping service provider: some trusted timestamping service providers offer web-based interfaces, where users can drag and drop files to have them timestamped. This works well with a variety of file types, including PDF documents. freeTSA is one example of a public timestamping service.
A matter of trust
Trust is the foundation upon which various standards and processes are built in the digital realm.
For instance, in the context of the OpenID Connect protocol, the relying party places its trust in the Identity Provider to ensure the accuracy and authenticity of the supplied identity information. This trust is at the heart of secure user authentication and authorization.
Similarly, the trust in the Time Stamping Authority is the core of trusted timestamping. Organizations rely on TSAs to certify the precise timing of digital transactions and to guarantee the integrity and authenticity of timestamped data. This trust is essential for legal, regulatory, and security purposes.
The regulatory aspect includes creating and maintaining lists of qualified service providers in legislation such as European Union Trusted Lists (EUTL) or Adobe Approved Trust List.
Use cases for trusted timestamping
Trusted timestamping can be applied in:
- Legal contracts and notarization: Trusted timestamping ensures that contracts and documents retain integrity and validity over time. This has far-reaching implications in disputes and litigation.
- Intellectual property protection: Trusted timestamping is a practical way to claim proof of ownership and invention for patents and copyrights.
- Financial fraud prevention: Trusted timestamps help businesses detect and respond to unauthorized alterations and potential fraudulent activity in the financial sector.
- Software development: For instance, timestamping can mitigate issues related to machine clock drift. This is especially valuable in open-source projects, distributed collaborations, and scenarios where code changes need to be audited or validated for compliance.
- Document signing: Trusted timestamping is a critical component in Public Key Infrastructure (PKI)-based electronic signatures, including PAdES-compliant digital signatures. These signatures rely on a combination of a trusted timestamp and proof of the signer's certificate validity (often in the form of an Online Certificate Status Protocol, OCSP). The two factors guarantee the long-term integrity and tamper-evidence of the signed document.
A trusted timestamp proves that the signed data existed at the given time. Combined with a digital signature, this additional level of security assures the authenticity of the signed data and protects against unauthorized changes. This common use case finds applications in several industries.
Summary
Including a trusted timestamp in digital documents ensures their long-term validity and establishes non-repudiation. It serves many purposes, from organizing information chronologically to making sure contracts are legally binding.
As more industries shift to digital platforms and replace conventional pen-and-paper signatures with digital signatures, the demand for timestamping will continue to grow. It remains a critical tool for enhancing the accuracy and integrity of digital transactions.



